Some cyber attacks are effective in an instant, achieving at least part of an attacker’s goal with just a single click on a bad thing, or similar quick fire delivery methods.
In an enterprise environment, the classic example is when a user clicks on a malicious link or opens a malicious attachment - then bad things start happening immediately, like malware getting installed on the user’s system.
Ransomware attacks, one of the most common and lucrative cyber attack types, often fit into this rapid fire and result category too. In these cases, the bad thing that happens very quickly is that essential data is encrypted and made inaccessible - and not just the single user’s data, this can impact data across an entire organization.
There are other cyber attacks that use radically different tactics in order to play a long game. These attacks will achieve the adversary’s goals as a slow, cumulative process. They may also be designed for a delayed final impact, saving the worst for last and ready to blow up (so to speak) at a time that is most advantageous for the adversary and most damaging to the victim organization.
These stealthy, long game attacks are often carried out by adversaries labeled as an Advanced Persistent Threat (APT). There are numerous good descriptions for APT, but Wikipedia’s entry is solid here:
An advanced persistent threat (APT) is a stealthy threat actor, typically a nation state or state-sponsored group, which gains unauthorized access to a computer network and remains undetected for an extended period. In recent times, the term may also refer to non-state-sponsored groups conducting large-scale targeted intrusions for specific goals
Thanks for reading Cyber Sherpas! This post is public so feel free to share it.
Living off the Land - or, in fancier cyber-speak with a fun acronym, Living off the Land Binaries, Scripts, and Libraries (LOLBAS) - is a core tactic for long game attackers. They want to minimize the “noise” they make in the victim’s environment in all but the final stages of an attack. Noise in this case means alerts generated in security tools that can make the cybersecurity team aware of their presence.
So how does Living off the Land work?
This tactic makes use of the built-in functionality of the operating system (OS) and built-in tools, binaries, scripts, and libraries that are native to the OS in target environments. A couple of the biggest advantages of this approach are:
- The adversary does not have to install malicious software (malware). This saves effort and makes attack activities much more difficult to detect for many security detection tools.
- Native elements of an OS like these are often ignored / whitelisted within detection tools.
Examples of Native Tools Used for Living off the Land
Here’s a short list of some of the most commonly used native, built-in tools for living off the land in a Windows environment:
- PowerShell: a scripting tool that is a core component of the Windows OS
- FTP: a file transfer protocol built in to Windows and other operating systems
- DNS: the domain name system that translates company network device names and website names to IP addresses to allow traffic to them. DNS is often used to exfiltrate (transfer out) data from a victim’s network.
- BITS: Another file transfer service - Microsoft’s Background Intelligent Transfer Service - which will be whitelisted by security tools and allowed through firewalls.
- Scheduled Tasks: Another handy and versatile built-in tool that will fly under the radar of many detection tools.
- WMI: (Windows Management Instrumentation) - Microsoft's core technology for managing and monitoring Windows-based operating systems.
There are many more of these LOLBAS tools, and the list is continually growing as adversaries refine their craft in this area.
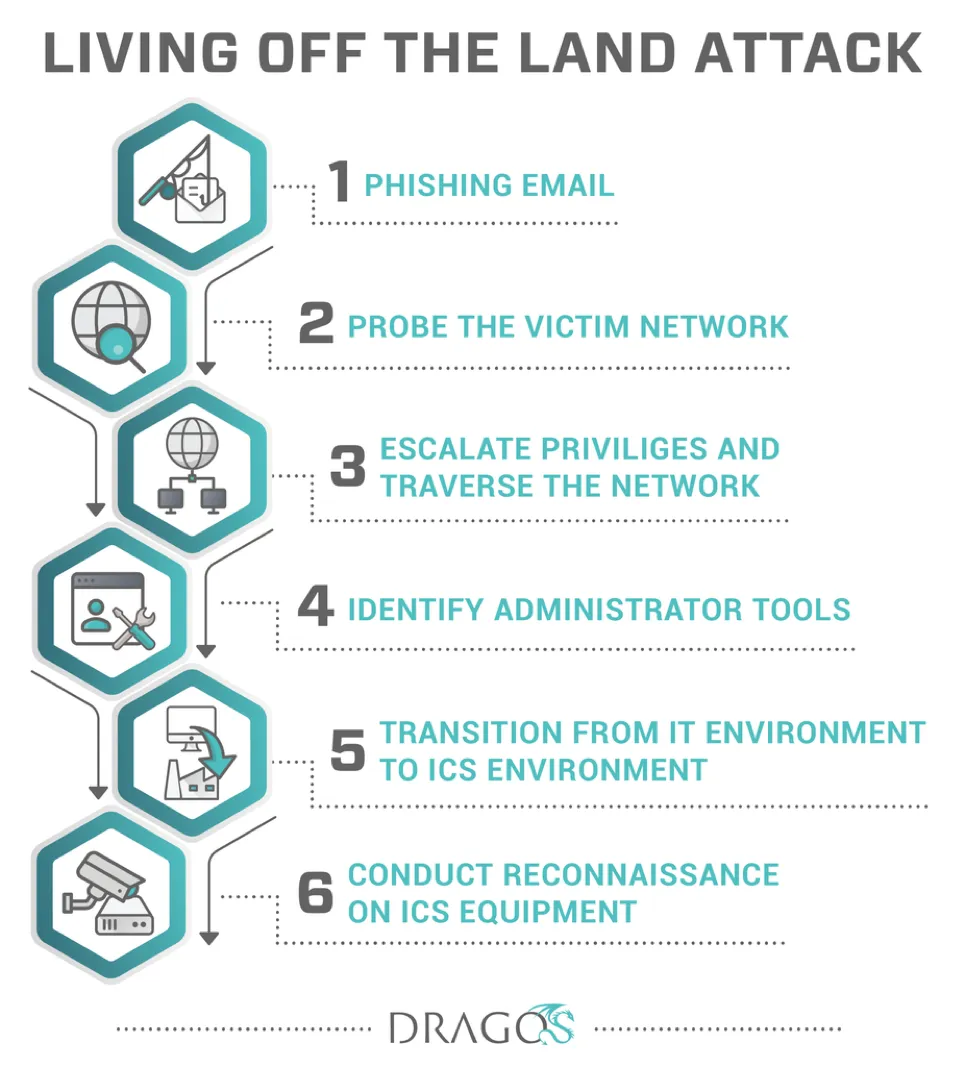
Note: The image at the top of the post, via Dragos, includes transition, or movement, from the IT environment to the ICS environment - as Dragos are a leading firm in the ICS Security space. The final stages of a Living off the Land attack will often be within the IT environment.
I hope that this overview of Living off the Land is useful and I am going to look to share a few more posts on cyber terms in coming weeks and months.
Thanks for reading Cyber Sherpas! Subscribe for free to receive new posts and support my work.
Member discussion: